Are you ready to bring your Bluetooth speaker’s full potential to light? Take your speaker to new heights by exploring the fascinating world of hacking!
We will walk you through the thrilling process of hacking your Bluetooth speaker, revealing a world of opportunities. You can turn your ordinary speaker into a potent instrument with the correct information and skills.
Prepare yourself to enter the fascinating world of Bluetooth speaker hacking and realize the full potential of your gadget.
Understanding Bluetooth Speaker Technology
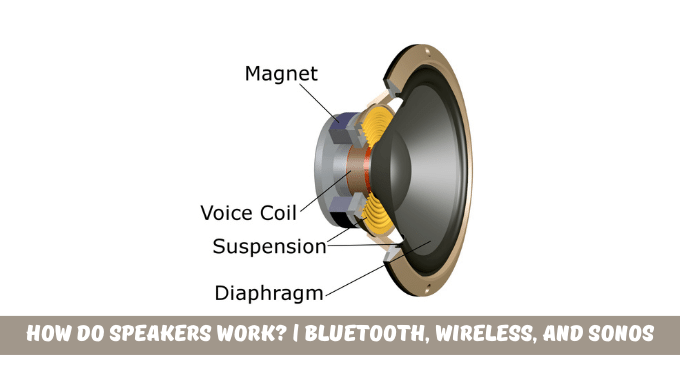
Bluetooth technology has distorted the way we listen to music.
Bluetooth speakers use short-range wireless messages when joining a device like a laptop or a smartphone. They receive audio signals from the connected device via a Bluetooth chip. They transform those signals into audible sound waves. The speaker and the device exchange unique identification numbers during the pairing procedure to establish the connection.
Hackers have discovered ways to get unauthorized access to Bluetooth speakers by taking advantage of flaws in the technology. It can be accomplished through strategies like the KNOB attack. The assailant intercepts the essential negotiation process between the speaker and the linked device. The attacker can take control of the speaker, play unlawful music, or even put spyware or malware on it. They can do this by pretending to be the speaker or interfering with the transmission.
To safeguard yourself from conceivable hacking attempts, comprehend the technologies underlying Bluetooth speakers. Leverage Bluetooth ease with audio security intact: stay informed, update software, and employ robust, unique passwords. Caution rules connecting to unknown or unsecured devices for a safeguarded audio journey.
How to Hack a Bluetooth Speaker?
You must only follow a few basic steps to hijack a Bluetooth speaker and control its features.
- The target device’s MAC address and other necessary details must first be gathered.
- You can find this by searching online or seeking nearby Bluetooth devices.
- You can set your laptop as a contact point and claim possession of the target device’s MAC address after you see the MAC address.
- You can introduce a man-in-the-middle attack when the aiming device joins your access point and issue commands on its behalf.
- The maneuver can then be infected with malware or spyware without the user’s information.
- It’s crucial to remember that this technique needs an iPhone with iOS 11 or above loaded.
Remember:
These instructions make it simple to hijack a Bluetooth speaker and take over its features. However, it’s essential to apply this information ethically and responsibly. It’s unlawful and a privacy infringement to hack or take control of someone else’s Bluetooth speaker without that person’s consent. It’s crucial to constantly respect other people’s boundaries and get permission before engaging in any hacking actions.
How to Hack Bluetooth Speakers with iPhone or Android?
You can take over a standard wireless audio device, like a Bluetooth speaker, without authorization by using the KNOB attack.
What is KNOB?
The KNOB attack enables you to take control of the speaker’s connection and issue commands on the target’s behalf. It indicates that no permission is required to play music over the speaker. To ensure interoperability, Bluetooth devices come in a range of security settings.
The technique drastically reduces security by forcing weak encryption. Weak encryption delays down changes, making connection hijacking simpler for neighboring hackers. To successfully end the handshake, the attacker must be close enough to stop it physically.
How does it function?
It’s not cool, but it is probable to hack a Bluetooth speaker.
- Utilize a KNOB attack exploit
- Amplify using MITM setup
- Use a Python script to modify packets to break the link.
- Use Btscanner in Kali Linux to hack the speaker for direct access without pairing.
- Start the Bluetooth service
- Launch BT Scanner
- Adhere to instructions, and control the selected device to do tasks like playing music.
Are Bluetooth Devices lack security?
Users of Bluetooth devices are exposed to possible security breaches and unauthorized access due to the device’s weakness. With the development of hacking methods and tools like bluez0r, it is now simple for hackers to create programs that interact with Bluetooth speakers. They play unlawful music or even set up malware or spyware without the user’s knowledge or approval.
Because Bluetooth devices lack security, there are numerous ways for hackers to take control of or break into these speakers.
Users must know the security dangers associated with Bluetooth devices.
Manufacturers should prioritize security measures to protect consumers’ privacy and stop illegal access.
Exploring Advanced Hacking Techniques
Learn about the fascinating realm of sophisticated hacking techniques.
You can go into Bluetooth speaker hacking’s depths and push the envelope of what is feasible. Imagine completely controlling your Bluetooth, modifying its settings, and adding sets and original sound effects. You may unlock your Bluetooth speaker’s full potential and create a unique musical masterpiece by diving into advanced hacking techniques.
But always keep in mind that with tremendous power comes great responsibility. When you experiment with these sophisticated hacking tools, it’s crucial always to put ethical use and regard for others’ privacy first.
As a result, there are many possibilities for personalization and management when a Bluetooth speaker is hacked. You can make your Bluetooth speaker into a multipurpose gadget that does more than play music.
Conclusion
Attackers are particularly interested in hacking these devices because Bluetooth is a widely used feature on most modern devices. Everyday uses of Bluetooth products include pairing them with headsets and car speakers. To prevent these attacks, educating individuals and groups about Bluetooth security is essential.
If an attacker can gain access to your device, they will be able to spy on your communications and manipulate and steal sensitive data. Bluetooth will continue to be attacked by existing attacks or zero-day vulnerabilities. Try to prevent attackers from easily hacking your Bluetooth device because people are addicted to their phones and tend to store various information there.
FAQs
How to Use Termux to Crack a Bluetooth Speaker?
There is a terminal emulator app called Termux for Android and other Linux-based platforms. You need a rooted Android device to use this app to hack Bluetooth speakers. Use the same procedures as you would with Kali Linux to hack a Bluetooth speaker using Termux.
Why Is It So Difficult To Hack Bluetooth?
As we already mentioned, hacking a neighbor’s Bluetooth speaker might be more complex. It is because Bluetooth hacking demands your presence during Bluetooth device pairing. Otherwise, you have to force the devices to pair again.















Leave a Reply